What is AppLocker
What is applocker and why sistem administrators need this tool
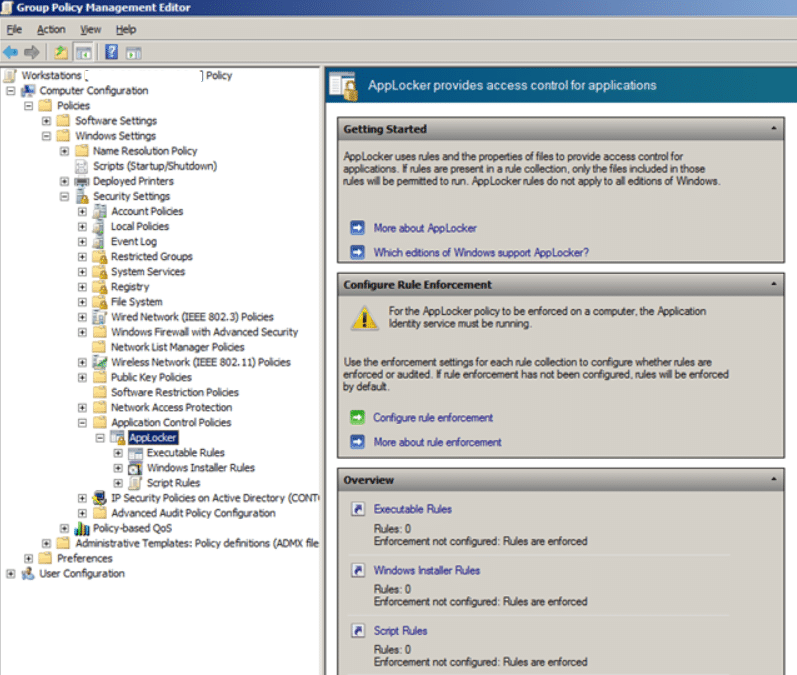
What is AppLocker? Applocker is a new technology in Windows 7 that allows a system administrator to block the execution of certain executable files on computers on a network. AppLocker is an extension of the Software Restriction Policy technology (used in Windows XP / Vista), but the latter could block the execution of programs based only on the file name, path, and file hash. AppLocker now has the ability to block executable files based on their digital signature. As a result, you can block programs based on the program name, version, and vendor. This means that if the manufacturer updates the version of the program, the AppLocker rules will continue to block the updated application, thereby reducing the burden on the system administrator. Also, for example, you can create an AppLocker rule based on the software version, thereby allowing you to start only certain previously allowed versions of software. Another advantage of AppLocker is that now it doesn’t matter where the program runs from (even from a memory card), AppLocker will block the launch of the program anyway.
This method of blocking the execution of certain programs using AppLocker can be used to block the execution of any executable file released by Microsoft or third-party developers. In this example, we will try to prohibit the use of the Google Chrome browser using group policy and AppLocker technology (I take this browser for example only, and not because of dislike for it, as many might have thought).
How to use AppLocKer?
- Open the GPO that is applied to the target computers. Open the Computer Configuration> Policies> Windows Settings> Security Settings> Application Control Policies policy and select the “Configure rule enforcement” option
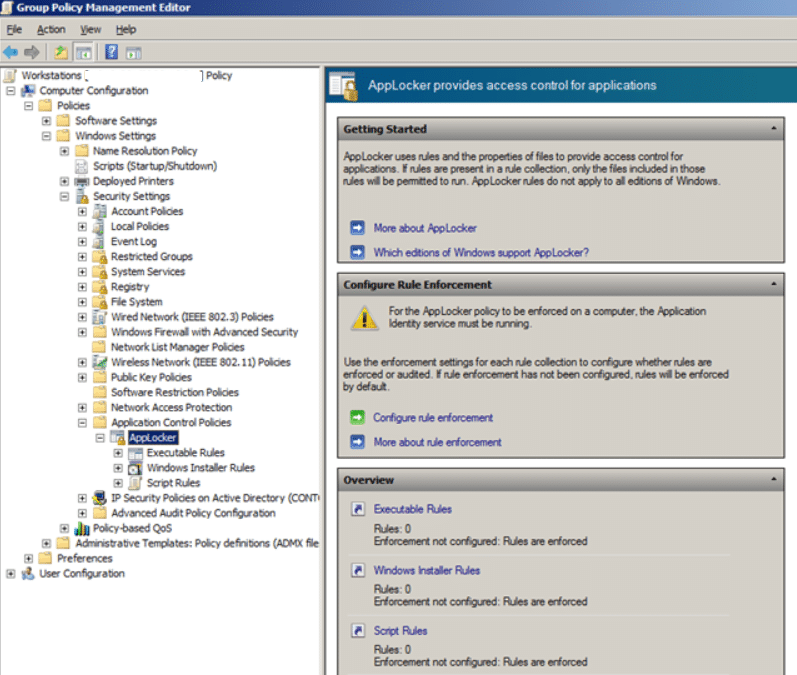
Related post : What is System32 folder in Windows and May I delete System32…
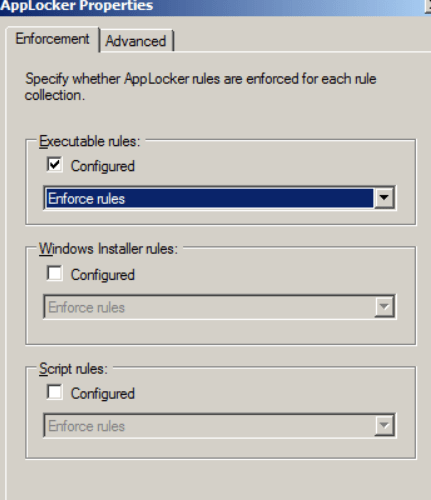
- In the Executable rules section, check the “Configured” option and select “Enforce rules”, then click “OK”.
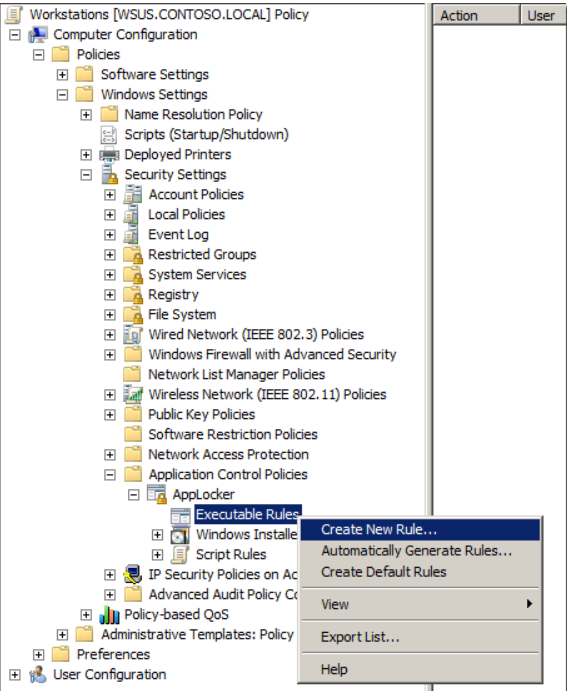
- Right-click on “Executable Rules” and create a new rule “Create New Rule.”
- Click “Next”
Related post : LSASS.exe: what is LSASS.exe process and how LSASS.exe works in…
- Select “Deny” and “Next”
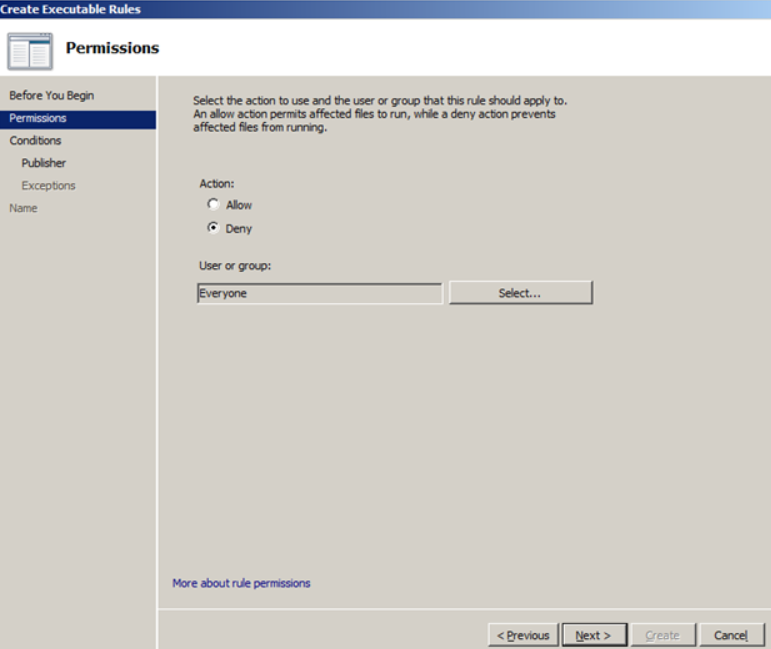
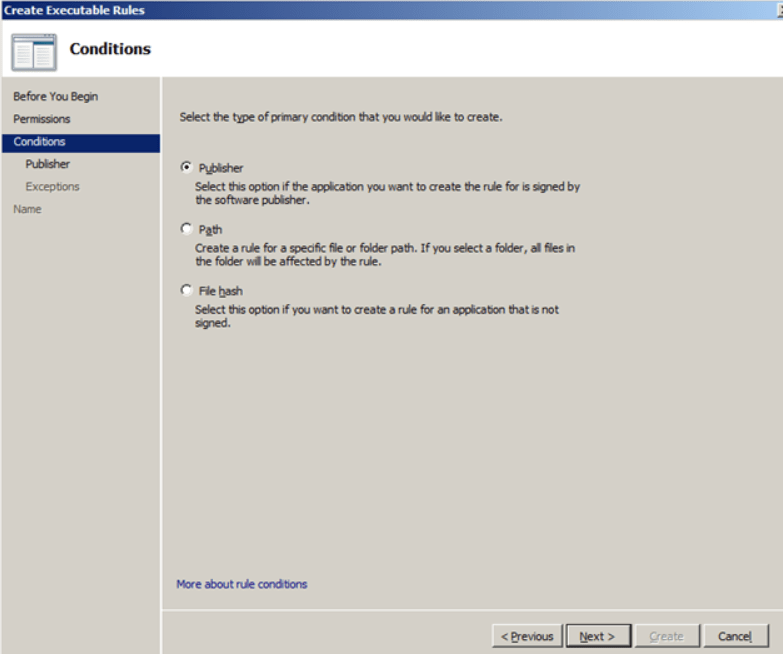
- For condition (condition), select “Publisher” (publisher) and click “Next”
Note: The “Path” and “File hash” options follow the rules used in Software Restriction policies in Windows XP / Vista.
Related post : Perform a clean boot in Windows 10/8/7
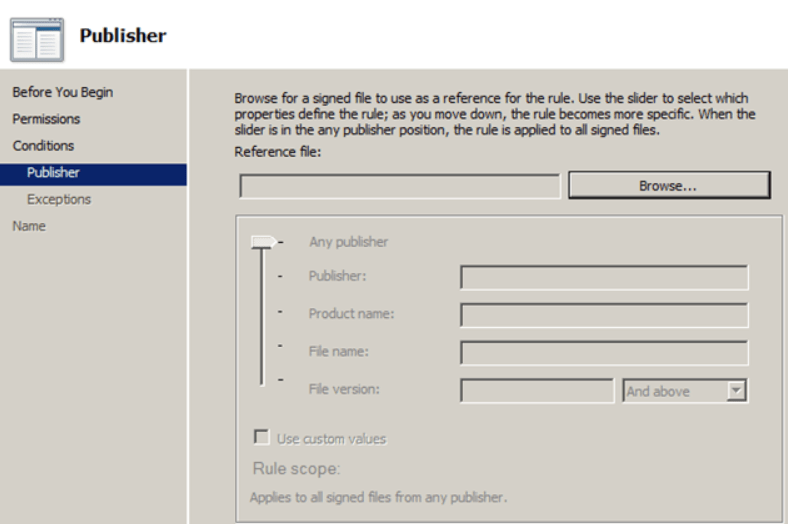
- Click “Browse” button.
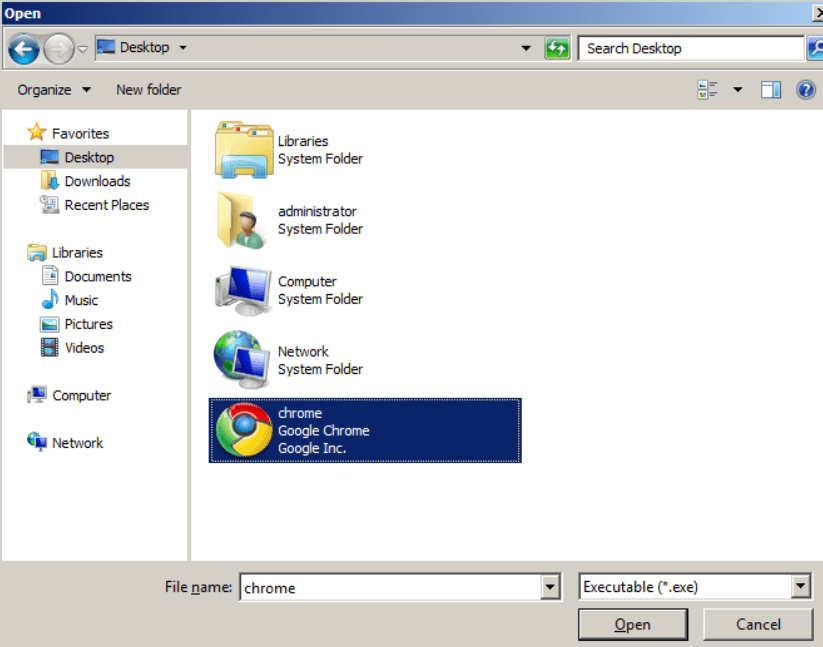
- Select the Google Chrome executable file “chrome.exe” and click “Open”
Related post : BOOTMGR is compressed.What to do.
- In this example, we will be satisfied with the default settings, so just click “Next”.
Note: If you want to block a specific version of the program, then tick “Use custom values” and in the corresponding field “File version” set the version number, the use of which you want to block with this policy.
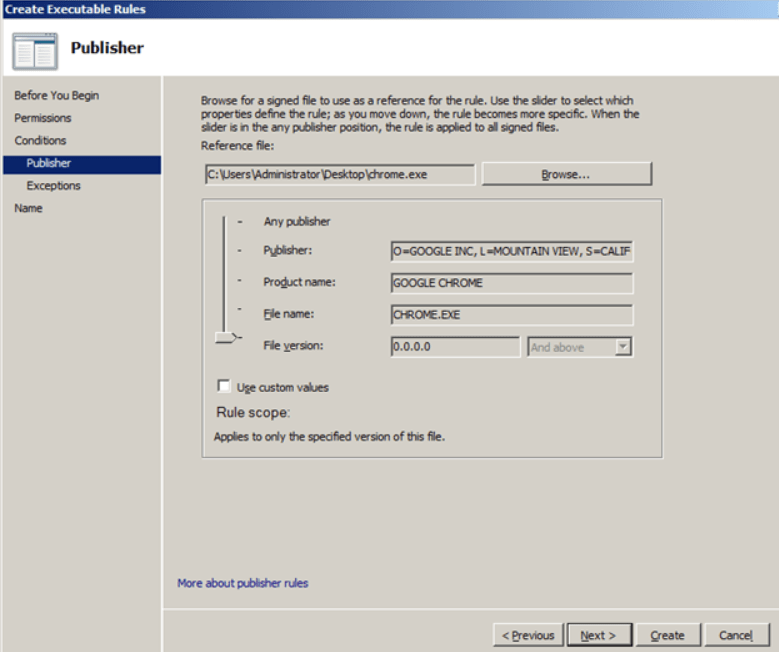
- 10: Click “Next”

Related post : Windows SFC
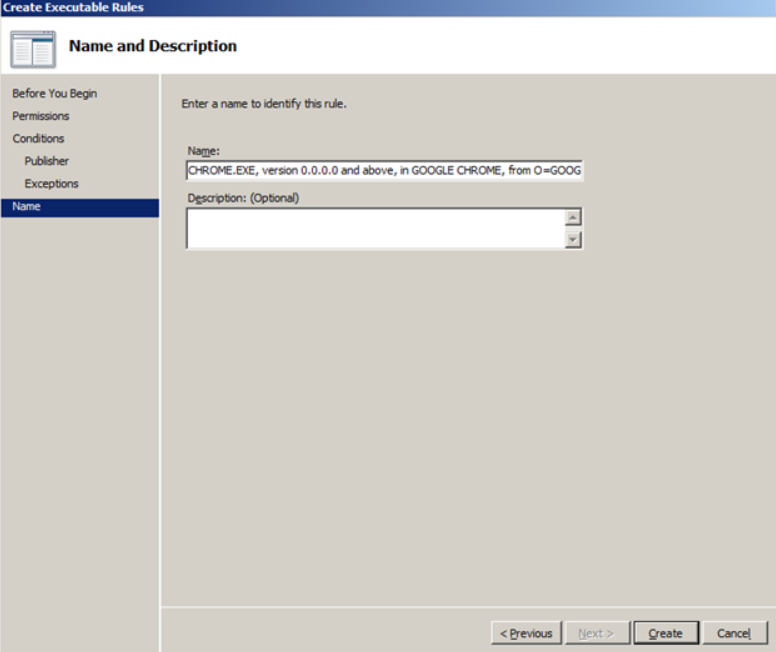
- 11: And finally, create a rule – “Create”
Related post : Fix WHEA_UNCORRECTABLE_ERROR error in Windows 10
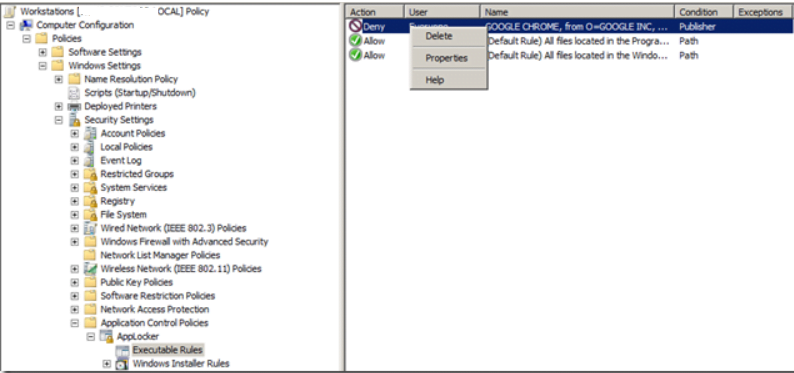
- 12: If you want the AppLocker rules to be applied to the computers of administrators, in the right pane, select the rule for “BUILTIN \ Administrators” and delete it
Related post : How to create software RAID in Windows
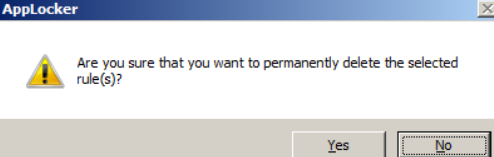
- 14: We answer “Yes” to the request
Related post : How to find your wireless network password
Now our AppLocker rules are configured and look like this:
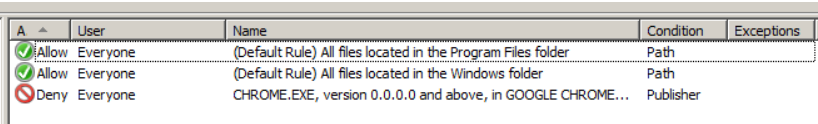
Related post : How to find a printer IP address
The last thing we need to do is activate AppLocker on target computers.
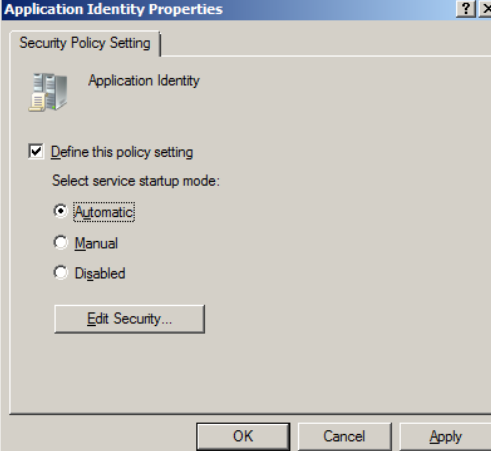
- In the same group policy, go to the Computer Configuration> Policies> Windows Settings> Security Settings> System Services branch and double-click on the “Application Identity” service.
Application Identity is an application that, before launching any executable file, performs its scanning, identifying its name, hash, and signature. If this service is disabled, AppLocker will not work.

Related post : How to change the background of the startup screen in Windows…
16: Select “Define this policy setting” and “Automatic”, then click “OK”
Related post : How to disable USB ports on a Windows 10 PC
The system services section will look like this:
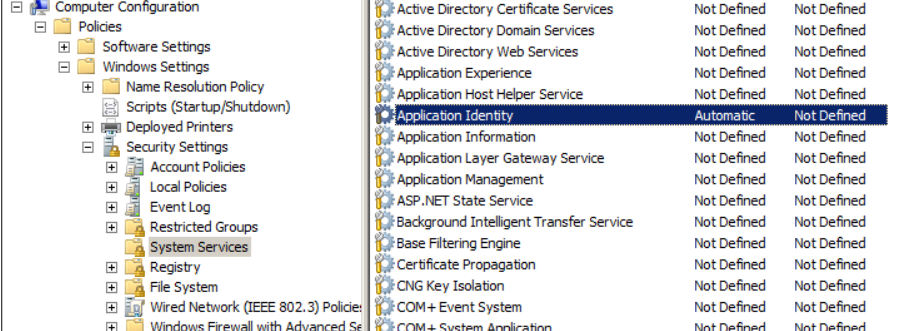
Related post : How to upgrade Windows 7,8 to Windows 10
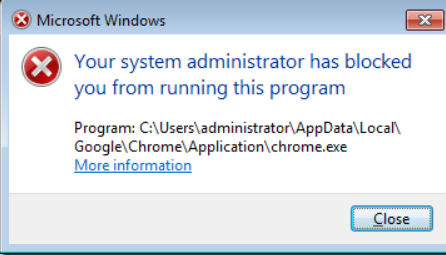
That’s all. After applying this policy, if a user tries to launch a banned application (in our case, this is Google Chrome), the following dialog box will appear: